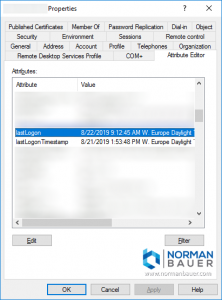
Yes, Active Directory provides details on when an active directory user last logged on. However, in a multi domain controller environment it may be tricky to get this information. If you’re on a single domain controller domain you can use Active Directory Users and Computers, navigate to the user, open its properties and go to the “Attribute Editor” (Advanced Features have to be enabled in the console). All you’ll need is the lastLogon property:
So, why lastLogon – what about lastLogonTimestamp?
Lastlogon is only updated on the domain controller that performs the authentication and is not replicated.
LastLogontimestamp is replicated, but by default only if it is 14 days or more older than the previous value.
(Source: serverfault.com)
That’s the reason why it is so simple to get that information if you have only one domain controller. When you have more than one, you have to get the dates from each of them and figure out the most recent date manually. You can do that by connecting to each domain controller, navigate to the user, open the properties, go to the attribute editor tab and read the lastlogon property. Nice, isn’t it? What if you have like a hundred DCs?
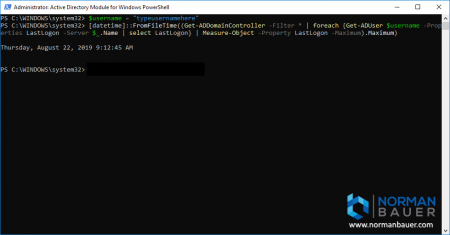
Powershell and the Active Directory Module can help you here! All we need is Get-ADUser, Get-ADDomainController and Measure-Object cmdlets. And because PowerShell gives you an Int64 FILETIME value, representing the number of 100-nanosecond intervals since January 1, 1601 (UTC) (source: docs.microsoft.com), instead of a nicely formatted date-time-value, we also need a datetime-function called “FromFileTime”:
Depending on the number of domain controllers this may take a few minutes!
What do we do here? We retrieve all domain controllers with Get-ADDomainController -Filter *. Then we query all DCs to get the LastLogon value of the user from each of them. After that we figure out what the most recent date is using measure-object. At last we convert the Int64 FILETIME value into human-readable format using the [datetime]::FromFileTime function.




Very helpful, Thanks
What about the logic needed to handle the scenario where the user has never logged on to a specific domain controller? I’ve been trying to use similar examples from other sources and the [datetime]::FromFileTime conversion appears to fail when there isn’t a normal date value. Could you expand your code to not only return a nicely formatted date/time string but also a string that says something like “No usage”?